Death and passwords: two things we just can’t avoid. With much of our life tied to cloud services these days, there is good reason to be concerned about what will happen to these accounts if we drop dead tomorrow. For many of us, important documents, photos, financial information, and other data will be locked behind a login prompt. Your payment methods will also expire shortly after, which could lead to data loss if not processed quickly. The most obvious way to solve this problem is to give access to a relying party in an emergency.
A bad solution
Let’s start with the simplest solution: use the same password everywhere. Great, all you have to do is put it on a sticky note, put it in an envelope and tell someone where to find it. Unfortunately, using a single password for many services is a very bad idea. Password breaches do happen, and if you use just one password on the Internet, they can be disastrous.
Password breaches are typically the result of an attacker finding a vulnerability that allows password data to be read from an application’s database. There is a good chance that your information was leaked in one of these breaches. You can check if your email is on a list of known violations with Have I Been Pwned. Don’t feel bad if you’ve been convicted, my email shows up on six different violations, and this service only indexes those violations that are known to the public!
Depending on the jurisdiction of the company that was breached, your password may have been stolen in several different formats. In the worst case, the passwords have been stored as is (i.e. in the clear) and the violation contains your actual password. These days, storing passwords in the clear is never considered acceptable. A hash of the password is stored instead. Attackers must use a tool like hashcat to try to recover passwords via brute force hash cracking. It’s slow for complex passwords, but it always gets faster as GPUs improve.
So we really have to use different passwords everywhere, otherwise our 2013 Tumblr account might give access to our bank account. Due to the large number of services we use and our inability to remember passwords, we will need to use a password manager.
You want a password manager
A password manager is a tool that allows you to securely store a large number of passwords. These will allow you to randomly generate a long and secure passphrase that you would never want to remember. This allows unique passwords to be used for each service and passwords that are complex enough to be difficult to crack.
We will also have to think about emergency access to these tools. How will someone be able to access your password manager and how can we protect this process? The goal is to create a backdoor to all of your accounts, and then make sure it’s reasonably well protected.
There are many password managers out there, and it’s not a matter of comparing them. In fact, security experts disagree on the best tools. To generalize, these tools fall into two categories: hosted and self-managed.
Hosted Password Managers
These are Software-as-a-Service (SaaS) tools that manage the storage of your passwords and provide access on all devices. Most will have desktop, mobile, and web extension clients. Firefox and Chrome both have built-in password managers which fall into this camp as well. Other popular products include LastPass, 1Password, and Dashlane.
These tools tend to be the easiest to use because all the data is handled for you. The downsides include subscription fees and the need to trust a third party with your password data. While most management services are designed so that only you can crack the password database, you should always trust the software they provide. In general, browser extensions for these services are considered less secure. For more on this, see Tavis Ormandy’s article on password managers.
When it comes to emergency access, many of these tools offer help features. LassPass and Dashlane both allow “emergency contacts” who can request access to your account. If you do not deny access within a specified time, access is granted. 1Password uses a low-tech solution, providing a printable emergency kit document that contains everything needed to access your account.
Self-managed password managers
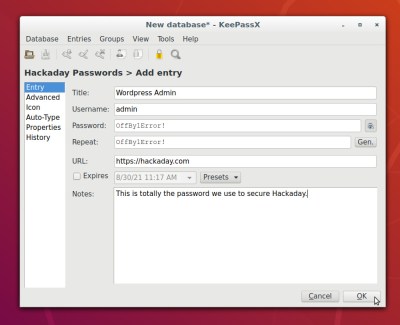
The other password management option is to manage your own data using local software. KeePass (and KeePassXC) and pass are two popular open source options. With these tools, it’s up to you to keep your password database secure and in sync between devices. It is also up to you to determine emergency access.
If you are going to use these tools, it is probably worth considering who will have access to them in an emergency. Will they be able to identify the required software, install it, access the database file and decrypt it? While the pass tool provides some cool options through gpg, such as using a hardware token for decryption, this added complexity can make emergency access more difficult.
If you’re using a self-managed solution, you’ll want to create your own version of the Emergency Kit to access it. This should include everything needed to view password data and instructions for accessing the encrypted password database.
Trust and storage
It goes without saying that you will need to trust the person you are providing emergency access to. Some hosted services provide functionality to minimize this trust by requiring a timeout before access is granted. For services that allow emergency contact, this means trusting the designated contacts. For solutions that require storage of an emergency kit, this means ensuring that only relying parties have physical access.
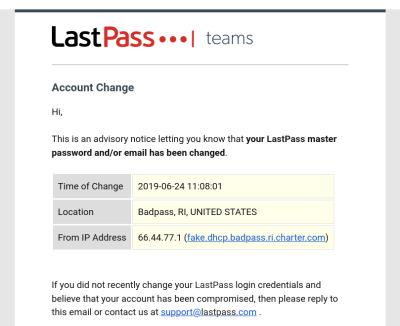
Another concern is whether emergency access has been used. If an attacker accesses your password manager without your knowledge, they can potentially maintain access indefinitely. Hosted services will provide notifications about new connections from unknown devices. For self-managed services, it’s up to you. Tamper-evident envelopes and boxes are an option, but they’re never perfect.
Remember 2FA
You have two-factor authentication (2FA) enabled on your accounts, haven’t you? If not, turn it on, we’ll wait here. If so, have you ever lost access to your authentication codes?
Some services will allow you to reset 2FA via email. It’s not great from a security standpoint, but it does mean losing your 2FA codes is a minor inconvenience. Other services make this process much more difficult. For example, losing all access to 2FA for Google requires going through a manual support process that can take days. It’s worth thinking about how someone might access your 2FA backup codes, at least for critical accounts.
No perfect solution
Providing emergency access will always make managing your passwords less secure, and that’s okay. In this case, we are compromising security for a specific and important reason. There is no perfect solution here, but the goal is to balance security and usability. This delicate balance is unfortunately inevitable when designing secure systems.

